
shark (shared risk)
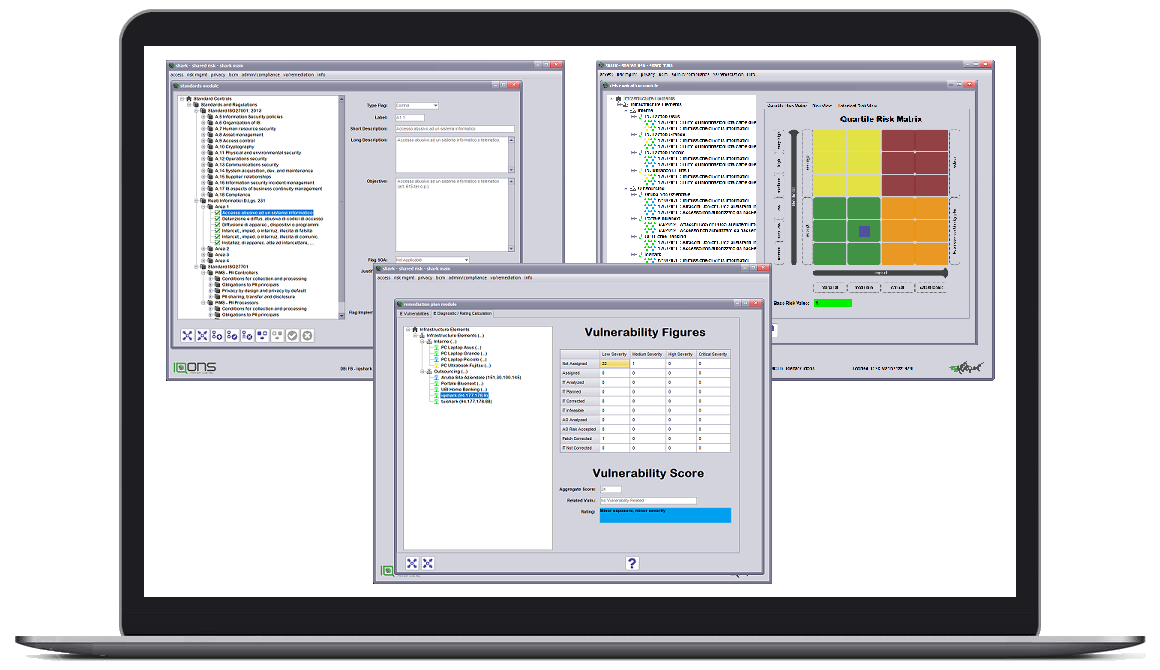
Information security management should be carried out following a double closed loop of control.
The first level is «logical» and directs the management of controls and technical and organizational countermeasures.
Control objectives are established, tasks are assigned and feedback is collected (governance).
The level of it risk for the company is then determined.
The second level is «physical» and is aimed at minimizing the attack surface, carrying out field measurements (va / pt) and managing the appropriate remedial actions.
Feedback on remediation activities determine the level of punctual risk (ip vulnerability score).
shark allows the evolution and integration of managed services by introducing new innovative "cyber security" services with high added value.
shark allows a logical "top-down" and physical "bottom-up" approach.
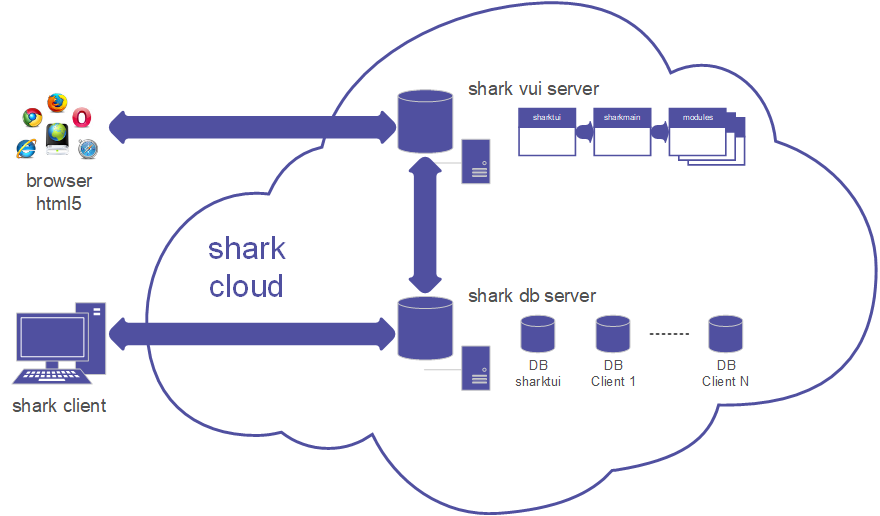
Each customer has a DB physically separated from the others and the data is resident in a cloud located in Italy.
A user can connect to multiple of a DB, but not at the same time: each connection has a separate logical access.
shark comes distributed in two modes: client / server (c/s) and web terminal server (wts).
The c/s mode provides the installation of the sharkage on each client and the connection through a specific port to the shark server.
The wts mode only needs an html5 web browser.




