shark site
Websites are vulnerable and are also the first image that companies have show on the network.
There are different types of cyber attacks on a website and some techniques they are used for the purpose of being able to change or modify some objects (images, javascript, scripts, links) contents
within the html pages that are loaded by users 'and customers' browsers; in addition to the html pages themselves.
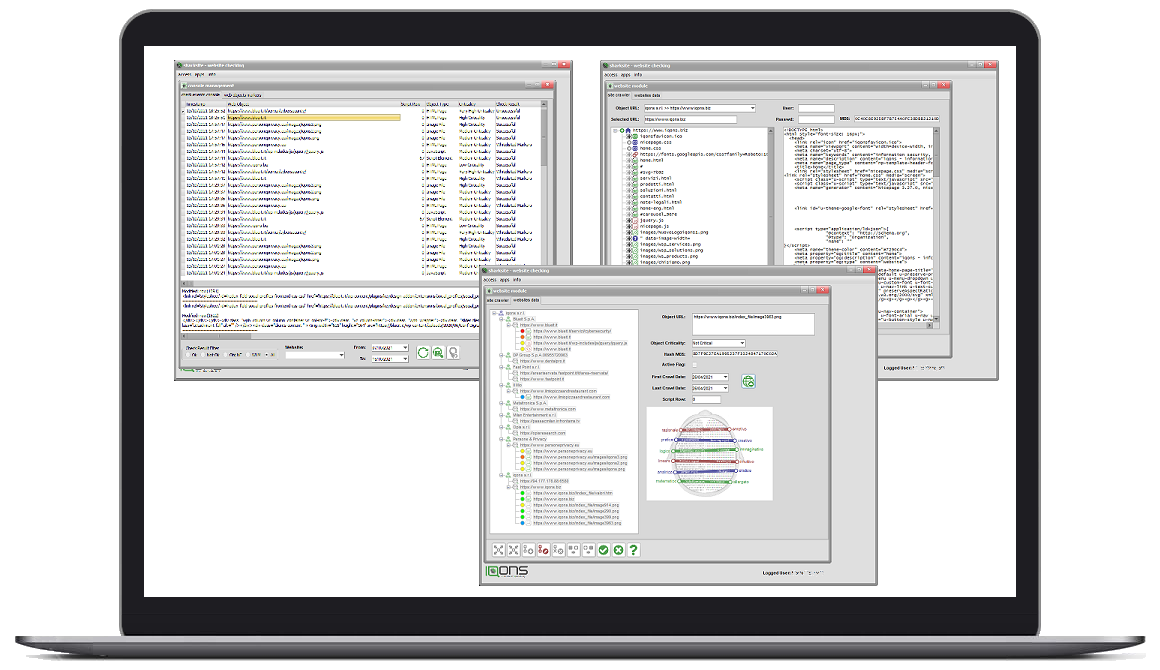
sharksite allows you to catalog the structure of a website and to select
the objects whose integrity you want to monitor.
A «web objects integrity checking» engine it then carries out periodic checks and alerts automatically if it finds changes on the website.
A console allows you to manage the
reports and alerting levels for each individual object surveyed in the «db checks».
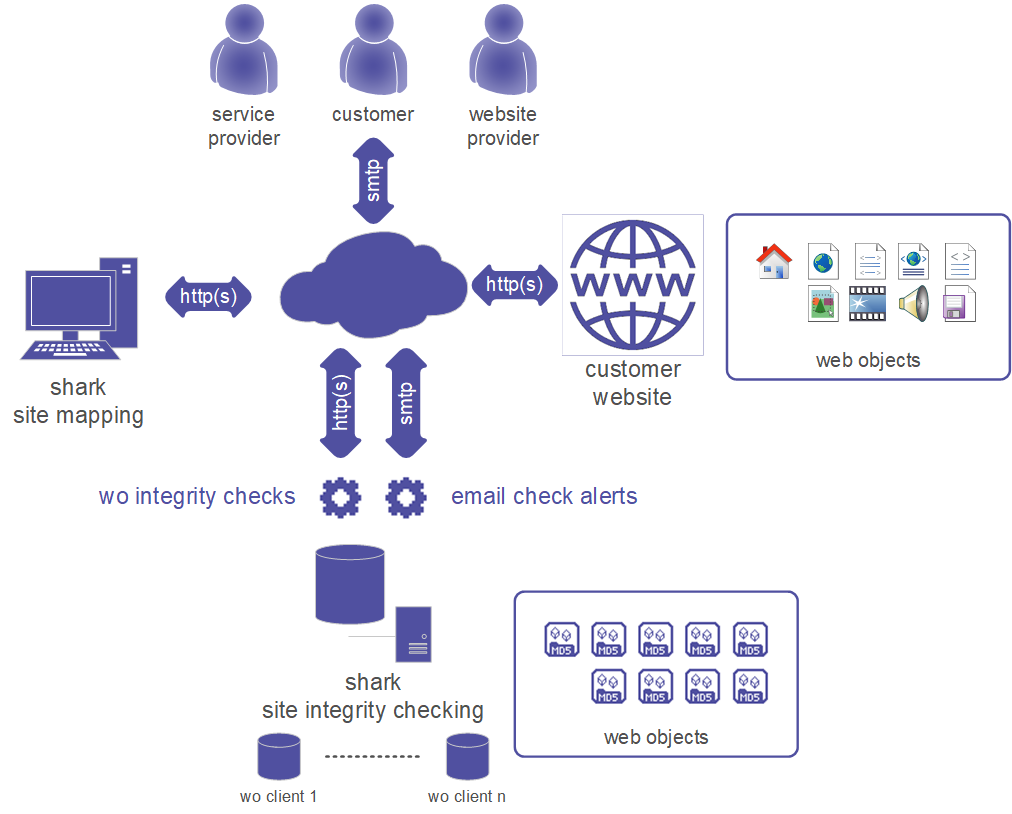
The service is based on a mapping of the website, in order to select the «web
objects» task of the next check.
An MD5 hash is calculated for each selected object and is used as the term of
comparison.
Once a mapping (or a mapping review) is done, the «web object integrity check» controls, on a regular basis, the integrity of the objects by recalculating the hash and comparing it with that original.
If any changes are found, they are automatically sent email to a predefined distribution list.
A console allows you to check the results of the checks and to modify the
checklist.




