cyber threat intelligence
Active monitoring, based on analysis and correlation of events (indicators), may not be sufficient: it generally does not allow the recognition of new attack techniques and is not able to predict the attackers' next moves.
Some precursors can come from Cyber Threat Intelligence (CTI) sources and can, if properly analyzed, predict a malicious action.
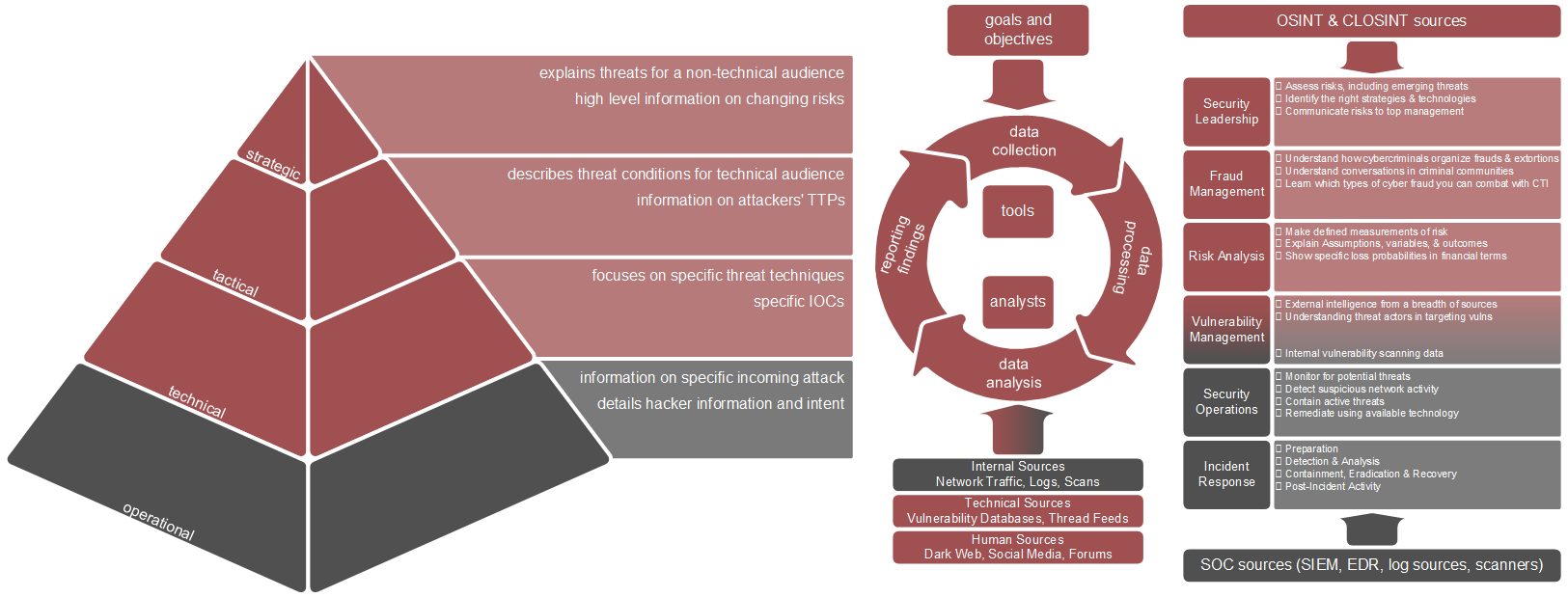
CTI is often defined as gathering information (adversaries and threats) relating to:
- intent: motivations and objectives of the attackers;
- opportunity: possibility for attackers to exploit vulnerability or other favorable conditions to achieve their objectives;
- capabilities: technical skills and resources used by adversaries to achieve their objectives by exploiting opportunities.
There is a lot of information available on the network which can be used for different types of attacks.
The service provided is non-invasive (beyond-the-firewall) and does not require technical information on the Customer's network and its potential attack surface.
iqons has developed a series of CTI services to help Customers prevent attack attempts where possible:
- research on the network, both in the emerged and underground parts, for information and vulnerabilities;
- search for documents left exposed on the web and analysis of the danger of the metadata contained.
- search for "look-alike" domains used for phishing attacks



